IPv6
Statistic
340
Undecillion IPv6 Addresses
4,3
Billion IPv4 Addresses
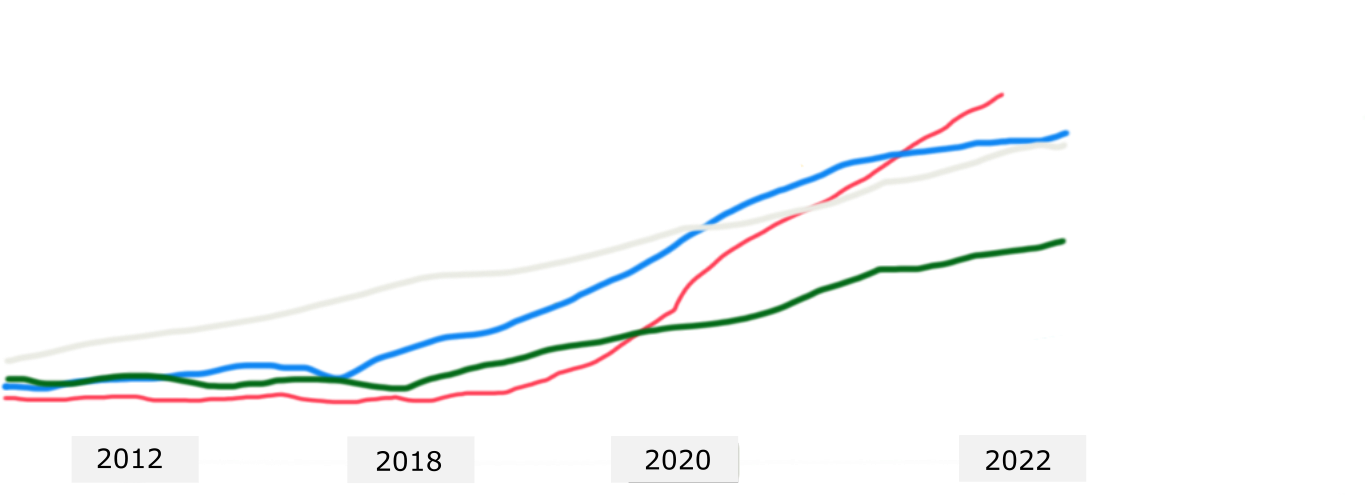
IPv6 Adoption in US Akamai
80% IPv6-Only in U.S Federal Space
IPv6 Adoption
As the price of an IPv4 address increases in 2018, and ISPs and cloud hosting providers are starting to charge more for IPv4 addresses while leaving IPv6 services free from additional charges for address space.
Google reports 49 countries deliver more than 5% of traffic over IPv6, with new countries joining all the time.Increasingly, IPv4 is an unnecessary cost, and a speculative asset.
In the six years since World IPv6 Launch, levels of IPv6 deployment in networks and service providers all over the globe have increased dramatically.
Over 25% of all Internet-connected networks advertise IPv6 connectivity.In the root domain, which is to say the service that provides the addresses for top-level domains (TLDs) such as .com, .org, .us, or .io, the twelve companies operating thirteen root server are dual stacked: IPv6 and IPv4 addresses.
IPv6 Evangelist
The advent of IPv6 changes not only the network components but also the security field shifts. We see new types of attacks or at least variations of the attacks we know from IPv4.
Through an analysis of your organization’s requirements for IPv6, GLADEV IPv6 Security engineers will determine which security techniques are possible and appropriate.
Our Architects will then help you to put together a practical secure design that meets your needs
Open source IPv6 Security Toolkits
The SI6 Networks’ IPv6 toolkit is a set of IPv6 security assessment and troubleshooting tools that can be leveraged to perform security assessments of IPv6 networks.
IPv6 attack toolkit.A complete tool set to attack the inherent protocol weaknesses of IPV6 and ICMP6, and includes an easy to use packet factory library.
Chiron – An IPv6 Security Assessment framework with advanced IPv6 Extension Headers manipulation capabilities.
IPv6 Deployment May 2022
- India
- Saint Barthelemy
- Belgium
- USA
- Germany
World IPv6 Deployment
- Americas
- Asia
- Europe
- Africa
—— Bahrain
—— India
—— Malaysia
—— Saudi Arabia
IPv6 STATISTICS 2023
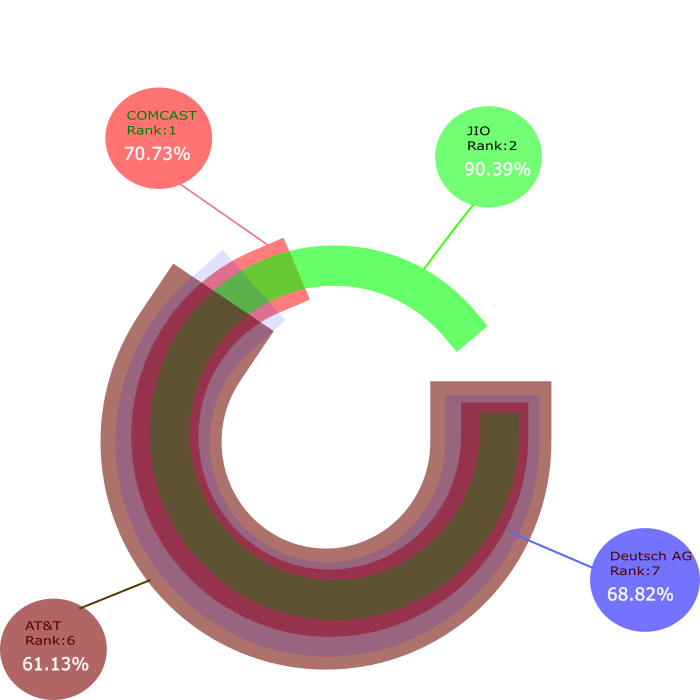
Network Operator Measurements
The IPv6 protocol can handle packets more efficiently, improve performance and increase security and GLADEV is here to help!
IPv4 Mapped
:ffff:0:0/96
Multicast
ff00::/8
ULA
fc00:/7
Link-Local
fe80::/10
Security in Design

Infoblox
IPv6
DNSSEC
Infoblox
IPv6
SOAR
Infoblox
IPv6
BloxOne
Infoblox
IPv6
DDI
This is an article by Vincentas Grinius of Heficed
In 2019, those responsible for the health and smooth operation of their organisation’s data networks are facing a new, creeping threat from the depletion of IPv4 addresses. Unlike the millennium bug, however, this threat has no defined deadline, no ‘high noon’, to encourage action.
This is an article by Vincentas Grinius of Heficed
In 2019, those responsible for the health and smooth operation of their organisation’s data networks are facing a new, creeping threat from the depletion of IPv4 addresses. Unlike the millennium bug, however, this threat has no defined deadline, no ‘high noon’, to encourage action.
This is an article by Vincentas Grinius of Heficed
In 2019, those responsible for the health and smooth operation of their organisation’s data networks are facing a new, creeping threat from the depletion of IPv4 addresses. Unlike the millennium bug, however, this threat has no defined deadline, no ‘high noon’, to encourage action.






